CYBERSECURITY, COMPUTING, OPTIMIZATION, AND NETWORKING
PJR has expertise experience in cybersecurity, networking, machine learning (ML), analytics, computing, software development, and T&E.
PJR’s experience includes developing research concepts & prototypes: ML plugin for SIEM, edge computing middleware, software/container hardening tool.
PJR has expertise experience in cybersecurity, networking, machine learning (ML), analytics, computing, software development, and T&E.
PJR’s experience includes developing research concepts & prototypes: ML plugin for SIEM, edge computing middleware, software/container hardening tool.
While AI, machine-learning, event-driven software architecture, and other types of automation tools represent the latest trends in technology, the reality is not so glamorous. A significant number of organizations, from government agencies to large corporate enterprises, are still tied to legacy applications that play a critical role in their respective operations. Enter PJR’s software transformation tool designed to address the issues that often plague legacy applications, costing organizations millions in terms of:
- Higher Sustainment Costs
- Difficulty Patching and Removing Known Vulnerabilities
- Not Yet Exploited Security Vulnerabilities
- Slow Execution
- Lack of Scalability, Flexibility
- Increased Power Consumption
- Poor Interoperability with Modern Technology
- Poor Customer Experience/Service
- Negative Impact on Employee Morale
Java DeBloat Video

Reduce your legacy application’s footprint by 20 to 60% without compromising features or functionality.
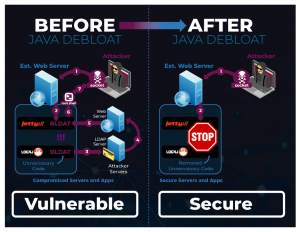
Software Transformation: removes dead code and features without needing to access source code or the original developers.
PJR’s software re-engineering system uses dynamic and static analysis to generate a call graph of the application, then applies slicing algorithms and cutting techniques to safely remove bloat and allow the user to selectively remove unwanted features from the compiled binaries. This results in smaller, simplified applications with less vulnerability.
Just like software, communication protocols can suffer bloat from numerous sources, such as support for legacy features and rarely-used/unnecessary functionality.
This bloat can represent significant problems to any organization, from increased security vulnerabilities to unstable communications and slower networks.
PJR partnered with a university to develop a protocol customization tool to identify, disable, and remove unwanted features of protocols. PJR takes a multi-pronged approach in simplifying protocols and maximizing their optimization:
- Protocol Feature Identification
- Feature-to-Source Code Mapping
- Automated Removal/Disabling of Features From Source Code
Less complication. Fewer security issues.
More speed and stability.
Protocol customization can address protocol risks and issues as they relate to mobile ad hoc networks, heterogeneous wireless networks, adaptive routing, reliable network transport, decentralized service operation and discovery, network management and monitoring, and cognitive network technologies.
With the ever-increasing demands placed on datacenters and other large-scale computing environments with the arrival of IoT, AI, and mobile computing, the need to create frameworks that can support more data-intensive applications is significant.
Model Driven DevOps (MDD) provides a means to leverage and scale existing networks to meet these demands, and more. . Automate and scale network configuration functions quickly, consistently, and securely using Infrastructure as Code (IaC)
MDD is the solution is the SDN solution network engineers have sought to handle the most critical networking tasks:
- Network Scalability
- Uptime
- Centralized Network Provisioning
- Holistic Enterprise Management
- Centralized Security
- Lower OpEx/CapEx
- Unification of Cloud Resources
- Data Traffic Control

As network complexity increases, organizations can either increase the support staff to manage the network, or deploy tools that absorb the increased complexity without the need for additional resources.
By automating a range of network configuration functions, MDD accelerates the delivery of new services, scales them in concert with demand, and replaces manual tasks with automated, repeatable processes.
The availability of ARM-based processors, Graphics Processing Units (GPUs), Data Processing Units (DPUs), AI accelerators is exploding, and Popcorn,, developed using Popcorn Linux Virginia Tech’s Popcorn Linux , enables applications to “pop” over to another ISA (and vice versa) without execution interruption. These emerging compute platforms are designed for specific types of applications and can be expensive and draw a lot of power.

Save money. Save power. Save time.
This has numerous benefits across the technology landscape:
- Developers can take advantage of the benefits offered by next-gen processors without rewriting applications from the ground up –potentially saving millions or even tens of millions of dollars.
- Server density can be increased as ARM processors require less power/cooling.
- Security posture can be improved.
The adoption of the open-source container platforms and third-party libraries provides significant cost benefits, but it also presents various security challenges. Containers can be exploited by an attacker using system calls to gain root access to systems operating on the tactical edge. Hackers can spoof/steal data, install malware, snoop network traffic or otherwise highjack systems.
Confine Video

Previous container attack surface reduction efforts rely on dynamic analysis and training using realistic workloads, and consequently are not practical or comprehensive. CONFINE only uses dynamic analysis to monitor the container to identify applications and relies on static analysis to identify the system calls used by those applications.

ABOUT PJR
PJR Corp is focused on providing tailored, innovative solutions to address cybersecurity and legacy software issues for the U.S. Armed Forces, and corporations both large and small.
It’s about commitment…
It’s about excellence…
It’s about innovation…
It’s about time… to expect more.
Experience the difference
that only experience can deliver.
PJR Corp brings over a century of combined experience to every engagement, every project, and every deliverable. As a woman-owned business, our company is solely focused on providing innovative solutions to address real-world cybersecurity and legacy software and protocol issues.
Trusted by the U.S. Military, and with expertise sought after by both large corporations and small businesses, PJR Corp tailors its approach to each engagement, ensuring a level of personalization and commitment unparalleled in the industry.
PJR Senior Leadership Team

Scott Harris
Lead Software Development
Leveraging his decade of experience with Qualcomm, Scott brings his expertise in leading our software development team. A compliance expert, Scott has developed and supported software applications with hundreds of thousands of users, as well as having transitioned complete software systems to be supported by a competitive software development team. He has a BS degree in Computer Science.

Hui Zeng
PhD in Electrical Engineering
Hui Zeng received his PhD in Electrical Engineering from the University of Maryland at College Park, majoring in communication (minor: control). Dr. Zeng has been working on management and technical lead of numerous projects funded by different government agencies (DOD, DOE, DHS, NASA) for the past 13 years. His research expertise encompasses all aspects of network (layer 2 and up) and security as well as various applications, such as network and cyber analysis, Big Data analytics, machine learning, deep learning, artificial intelligence, networking, wireless network, cellular network, cybersecurity, telemedicine, information management, and tactical cloud. He has authored/co-authored over 20 peer-reviewed articles in reputed journals and conferences and held 4 patents.

Eric Ortega
Software Dev/Scientist
Eric has filled senior technical and management roles in the aerospace industry, being responsible for multi-site software development projects with deliverables to original equipment manufacturers like Boeing and Airbus. While conducting research for his doctorate in Biomedical Engineering from University of Southern California and during his employment at a microscopy company, Eric wrote high-volume, heavily optimized graphics-processing algorithms that used probability models to perform data analysis.

Peter Allen Robinson
Founder and President
Peter launched PJR Corporation with the vision of creating and growing a company that provides innovative, tailored solutions to real-world cyber security and legacy software performance problems. Peter brings over 20 years entrepreneurial experience growing successful software companies and is focused on building PJR to include great people and products to serve a high-growth market.

Sandra Leigh Robinson
CEO
Sandra brings over a decade of experience and spearheads PJR’s banking, finance, advisor, and investment relationships. Sandra is involved in the day-to-day activities supporting employees, customers and partners while ensuring that PJR has the resources it needs to grow. Sandra is the point person for the many Federal agencies and systems necessary for PJR to perform on its contracts with the Department of Defense.
Talent hits a target no one else can hit;
genius hits a target no one else can see.
“We have a belief in what we’re doing, and a cause for which we are called. We are driven by purpose, and inspired to action. Each of us at PJR, in our own way, has taken hold of the opportunity to create something larger than ourselves. To be part of a unit that, collectively, impacts our clients in ways they expected – and in ways they could never have imagined.”
Peter Robinson
In the vast sea of legacy applications and cybersecurity threats, clients depend on PJR to provide them safe harbor. We’re not just software developers, computer scientists, and compliance officers, we’re the architects of optimization and the shield of cybersecurity.
Like a Special Forces unit, we operate in specialized teams, giving us the ability to be agile and nimble in tailoring the execution of our services to the precise needs of our clients. We do this with the understanding that meeting our objectives isn’t just critical, it’s mission critical.
If you’re ready to be a part of a close-knit team that supports each other in getting the job done; where your talent is respected and professional growth is part of the job description – then reach out and let’s have a discussion.
OPEN JOBS
Please check back for open jobs or contact us regarding career opportunities.